
Secure Onboarding
Control Your Connections with BYOD Made Simple
The adoption of smart devices such as smart phones and tablets creates two challenges for IT; network access and device security. Each category is unique and requires a different set of expertise and guidelines.
First things first the wireless network must be reliable; it is the foundation of your solution. Legacy wireless solutions were not engineered to deal with the high density and throughput required to sustain a fast and reliable wireless connection. The wireless network must be mobile device ready and designed for interference mitigation and high-density environments.
Furthermore, the Bring Your Own (BYO) device, application, and product such as a smartphone or and an apple TV to work, has created an environment where IT does not have control of the clients access the network. To salvage this problem many wireless companies have incorporated additional recognition intelligence that identify the user, type of device and application that is on the network and provide IT administrators the ability to create and enforce security policies. RUCKUS Networks solutions integrate this BYOD solution and provide an easy to configure and deploy solution that is low maintenance and allows end users to self-register their devices on the network.
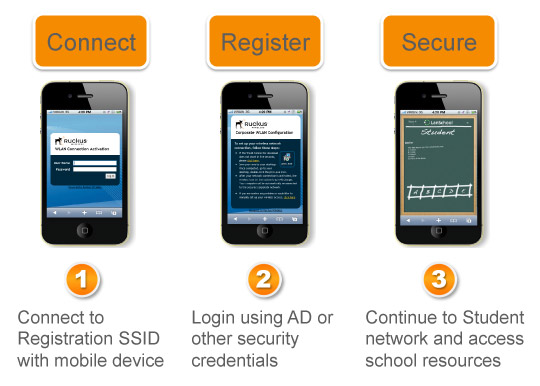
Hassle-Free Connectivity
Ruckus' CloudPath Enrollment System makes BYOD simple, seamless and self-service. Use a single point of entry to onboard practically any user-owned device, for any BYOD scenario—employees, students, partners or guests. With certificate-based onboarding, secure access is linked to the device, not just a user account. So people can onboard once and then automatically reconnect in the future—without having to constantly re-enter credentials.
Stress-Free Security
BYOD shouldn’t mean “bring-your-own-security-vulnerabilities.” CloudPath ES brings scalable, standards-based security to any environment, using the gold standard for enterprise wireless encryption. Configure your policies for different types of users and devices, and CloudPath automatically provisions them, without any manual IT intervention. You can even onboard “headless” devices like gaming consoles, printers, and video cameras to your Smart Wi-Fi network just as easily and securely.
Complaint-Free Administration
Thousands of different devices and platforms? No problem. Dozens of different use cases and policy profiles? Don’t worry about it. With RUCKUS secure onboarding, it all happens automatically. And you can use it seamlessly within your existing Wi-Fi and security environment, at a fraction of the cost of expensive 802.1x authentication systems. No more trouble tickets for each new kind of device. No more password headaches for your users and your helpdesk. Instead, BYOD just works. And your IT team can focus their time and attention where it’s needed most.
Handling BYOD with Ruckus
Integrated: RUCKUS has a fully integrated body of features to handle BYOD stress points for both administrators and users. First, we want to ensure that organizations can leverage their existing resources for BYOD enablement. To that end, we integrate with existing network segmentation and security architectures, authentication protocols, and directory services.
Purpose-Built: Second, businesses need purpose-built features to handle mobile device connection and security challenges. RUCKUS BeamFlex+ is specifically designed for mobile devices. The signal is directed only at the device, built-in polarization diversity maintains a strong signal regardless of device orientations, and ChannelFly ensure the devices receives the best possible path for higher bandwidth. For BYOD software, RUCKUS has built-in device provisioning and onboarding tools and workflows that are foolproof for users and simple to implement by IT staff.
Flexibility: administrators need flexibility to provide unique policies for specific device types. Our device fingerprinting and access control features provide this level of granular enforcement. The same device-specific awareness used to enforce policy is also brought to bear on monitoring and visibility to improve network operations, troubleshooting, and policy changes over time.
Finally, RUCKUS provides the RF stability, scalability, and capacity needed to enable BYOD. Robust wireless performance enables users to connect and stay connected, making BYOD initiatives work for the business.
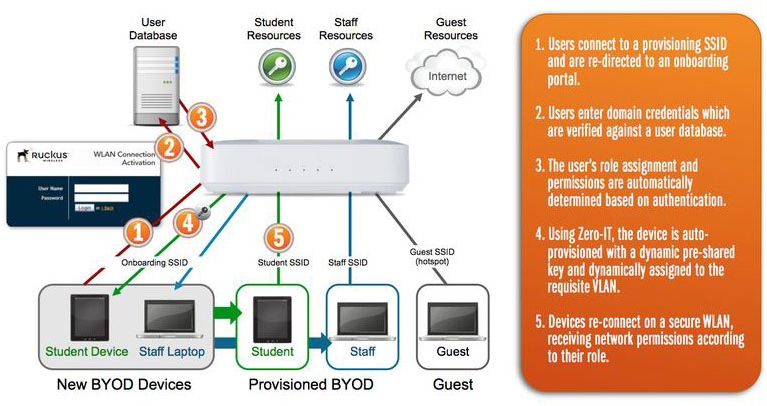
BYOD Features:
- Dynamic PSK offers a per-user PSK, which finds an ideal balance between 802.1X and passphrases. It’s easy to implement, but highly secure.
- Zero-IT Activation securely provisions and onboards wireless clients in an intuitive way, enabling network users to connect without IT staff interventio
- Directory Integration allows businesses to leverage existing directory investments—ActiveDirectory, LDAP, eDirectory—for BYOD device onboarding, user authentication, and policy
- Device Fingerprinting and Policy provides the flexibility to create authorization profiles based on user, role, and device type
- Client Visibility delivers granular monitoring and diagnostics so administrators and support staff can keep better tabs on, and make informed decisions about, usage trends and network behavior
- Pervasive Performance is a RUCKUS specialty. With unique features like BeamFlex, ChannelFly, and SmartCast, businesses can count on reliable connections and optimized mobile device capacity with fewer APs and less expensive solutions.

